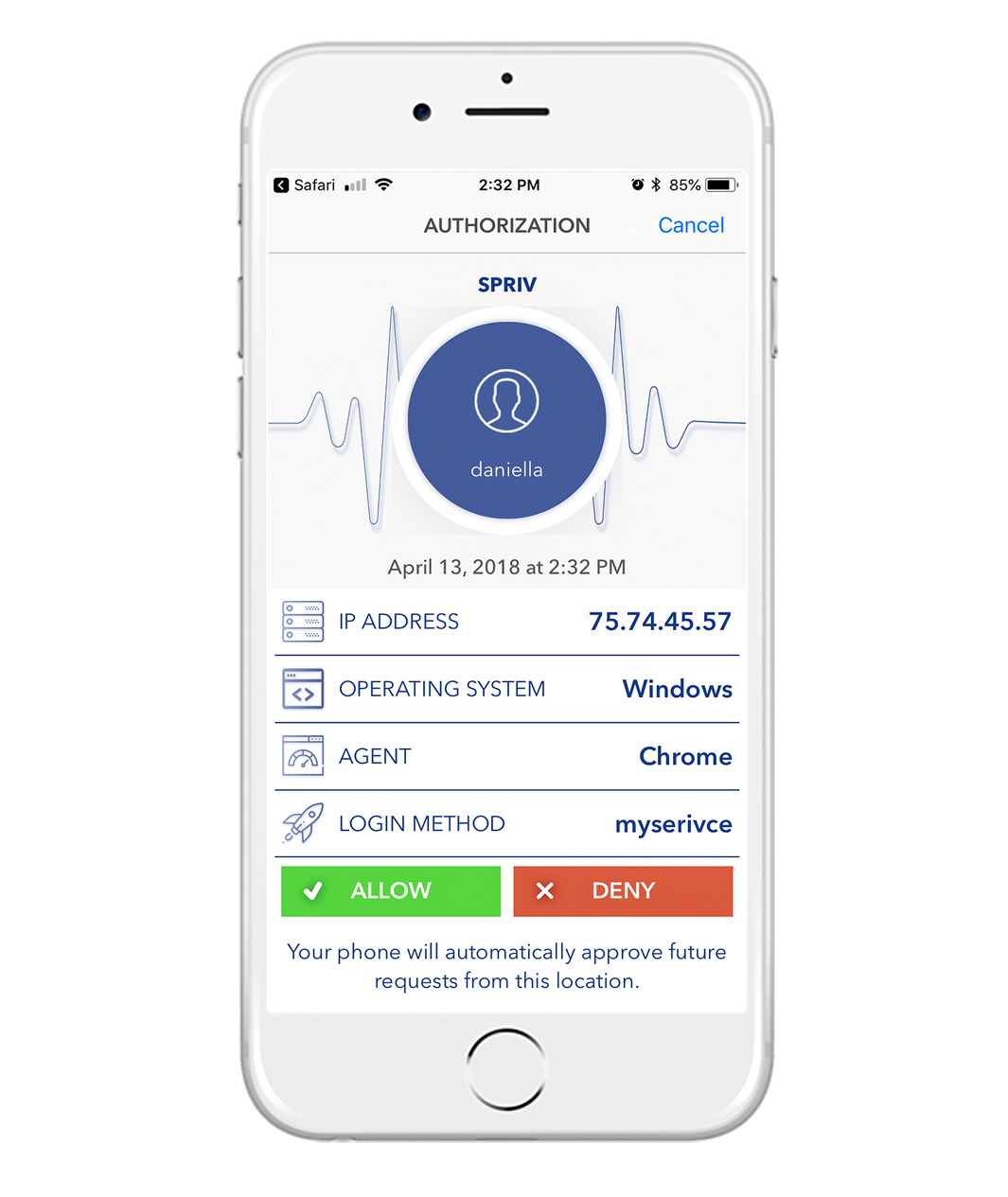
Risk Based Two Factor Authentication is a faster solution!
Spriv’s Risk Based Two Factor Authentication is a faster two factor authentication solution because it works in the background and requires no human intervention. Users simply login as they normally do and Spriv authenticates the information in the background multiple times and in multiple ways without any additional action by the user.
Simple integration, quick implementation and extensive management tools. Spriv seamlessly accommodates website security platform diagnostics and transaction authentication processes, instantly integrating with all leading enterprise applications. User operation and support are simplified with self-enrollment and management tools.
Since there is no extra hardware to purchase and maintain, offering Spriv to all employees, partners, and clients is highly cost-effective. Spriv authenticates transactions using a separate and independent hardware device similar to a hardware token but at a fraction of the cost with minimal upkeep and customer support expense.
Spriv defends against sophisticated attacks and hacking methods which defy other two factor authentication methods like hardware tokens, SMS, etc. Users are instantly alerted to any abnormal login attempt, for example: an unauthorized user uses username and password while the authorized user is more than five miles away.
User simplicity: Risk Based Two Factor Authentication is a faster solution because your users will be able to complete the Two Factor Authentication without getting the hardware token out of their bag!
Spriv’s patented technology allows you to automated two factor Authentication only if the phone fingerprint and the computer fingerprint from which the user entered his username and password match by Spriv’s Risk Based Authentication engine. For privacy reasons Spriv will not share the mobile phone data, but only verify that the computer and the mobile phone unique fingerprint match. If both fingerprints match, then Spriv will automatically approve the transaction. If the fingerprints mismatch, then the user would be able to decide whether he would like to approve or deny the transaction.
